Newly discovered flaws leave computers vulnerable to cyber-attacks
Source: Adaptiva
January 25, 2018
The security of people’s private information may depend on how often they update their phone or computer, as two recently discovered hardware vulnerabilities were shown to allow hackers access to computers’ secrets.
Computer security experts found that two hardware vulnerabilities, Meltdown and Spectre, can let hackers use malware to exploit computer processes and steal information stored on the system.
Meltdown and Spectre were birthed from a hardware process called “speculative execution.” Speculative execution is a behind-the-scenes action by computers that speeds up its work, according to Chris Fletcher, professor in Computer Science.
For example, if a computer speculates someone will get their password correct before they even click enter, it can have their account information to them even faster, Fletcher said.
Although Meltdown and Spectre work in similar ways, they are very different “beasts,” he said.
Get The Daily Illini in your inbox!
In the case of Meltdown, the flaw occurs in a small window, only nanoseconds long, when speculative execution is running and the operating system is left vulnerable. While the computer’s processor confirms whether it speculated correctly, hackers are able to access the operating system space to steal information, Fletcher said.
He added that hackers’ ability to access the operating system space of a computer completely breaks a desktop laptop’s security.
“This is a problem, since the system could then leak and compromise things like passwords or encryption keys,” Dana Mancuso, media contact for University Technology Services, said in an email.
Compared to Meltdown, Spectre is more difficult for hackers to exploit, Mancuso said.
Spectre works by exchanging information with programs that are not authorized to do so. It can cause a processor to misspeculate, and in some cases leak information it never intended, Fletcher said. This could be anywhere in the realm of passwords or less important information.
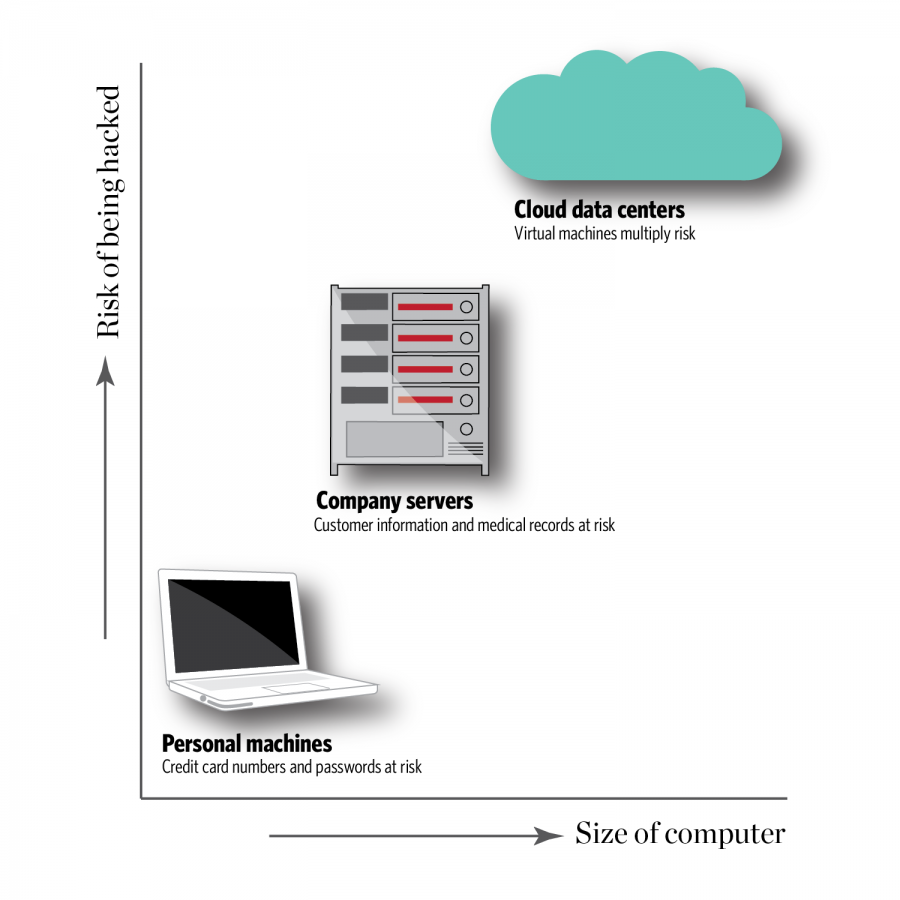
According to Adaptiva’s website, an IT management company, the security risk associated with Meltdown and Spectre can increase depending on the level of technology cyber-attackers choose to target.
On a personal computer level, passwords or credit card numbers could be accessed, according to the website. Through something bigger like a company server, a hacker could gain access to the customers’ personal information or medical records.
Adaptiva found if an attacker accesses a cloud network, the risk can multiply, as they can reach multiple people and companies.
The most important step people can take to protect themselves from these two vulnerabilities is to make sure their devices’ softwares are up to date, Fletcher said.
Since the discovery of Meltdown and Spectre, major system vendors like Lennox, Intel and IBM have been pushing out software patches to fix problems with Meltdown. People can also check to see if their system is up-to-date by visiting their company’s website and comparing their update numbers, he said.
Fletcher said the discovery of Meltdown and Spectre is something the tech community calls a “hardware zero-day,” referring to a software vulnerability that no one saw coming.
Once a concept, like the Meltdown or Spectre vulnerabilities, is disclosed, there are usually several weeks before hackers learn how to weaponize the concept. This makes updating computer software as soon as possible very important, Fletcher said.